
Lastline and SIRP – Automated Threat Intelligence and Network Detection and Response
September 18, 2020
Sumo Logic and SIRP – Beyond Traditional Cloud Security Monitoring and Incident Response
January 18, 2021
Lastline and SIRP – Automated Threat Intelligence and Network Detection and Response
September 18, 2020
Sumo Logic and SIRP – Beyond Traditional Cloud Security Monitoring and Incident Response
January 18, 2021Automate and Orchestrate Investigation and Response of Phishing Attacks
Dealing with the growing volume of cyber attacks, Phishing remains one of the most used methods of cybercrime to date.
Phishing is an attack that uses disguised email as a weapon. The goal is to trick individuals into providing sensitive data such as personally identifiable information (PII), banking and credit card details, or passwords. For instance, a request from the bank, or a message from someone in company to click a link or download an attachment.
Oftentimes, phishing emails are used to execute even more advanced attacks. For example, users would receive a legitimate-looking email that entices them to click on a link. Clicking on the link would run a malicious code. The malicious code could either execute a crypto mining job in the background or even compromise the system, allowing attacker access to the system and potentially the entire network.
85% of all organisations have suffered from a phishing attack at least once. Whether it’s an employee’s awareness or a security control (or both) that detects a phishing attack, it’s important to quickly report to the appropriate stakeholders, control the damage, and take response actions.
Challenge
- High volume of phishing emails
- 101 days to discover phishing related malware 
- Repetitive, manual and tedious actions to remediate phishing incidents
Solution
SIRP provides you with a playbook to effectively prioritize, investigate, and respond to phishing email threats. You can ingest reported malicious emails as Alerts into SIRP and run the Phishing investigation and response playbook. Since SIRP integrates with multiple security technologies such as sandboxing and threat intelligence, your phishing playbooks allows you to analyze files and retrieve threat intelligence on the URLs, domains, IPs and other artifacts that are automatically fetched from the suspicious email. Finally, based on the investigation results, the playbook will automatically take actions to mitigate the threat or escalate the incident for further actions.
Phishing Playbook
Following is the overview of the playbook workflow for the phishing email use case:
Stage 1 : Identification
When a phishing email is received, it is ingested as an alert into SIRP. Organizations can create a dedicated inbox where employees could send/report malicious emails. SIRP would read that inbox and ingest the email as an alert.
While ingesting a phishing email, SIRP also parses and extracts all the artifacts from the email including email addresses, email header, domain names, URLs, file attachments, etc.
Stage 2: Enrichment
The next step is to contextualize the event through artifact enrichment integrations such as different Threat Intelligence Platforms (e.g. VirusTotal, TIP, AlienVault, etc) and internal security controls (e.g. Active Directory, EDR, etc.)
These integrations help analysts gather information like URL’s reputation, File’s Sandboxing report, Header Analysis, or user’s information from Active Directory.
Here are is the list of enrichment actions used in the playbook:
Actions |
Description |
| get_file_reputation | Query a threat intelligence service for the file's reputation. |
| get_url_reputation | Query a threat intelligence service for URL’s reputation. |
| get_domain_reputation | Query a threat intelligence service for domain’s reputation. |
| get_whois_domain | Run whois query on the given domain. |
| get_url_info; | Query a threat intelligence service for a URL’s info. |
| get_domain_ssl_info | QUery a threat intelligence service for a domain’s SSL info. |
Stage 3: Investigation
At this stage, the playbook tries to check if the report email is actually malicious or not, if the attack was successful or not, and if any remediation actions should be taken.
Stage 4: Remediation
This is deemed to be one of the most critical phases; as this is where the damage of the phishing attack will be contained. At this stage, playbook could take various actions to remediate the threat such as blocking malicious IP on the Firewall, pushing the domain to SIEM’s reference set for future monitoring, or sending hash to EDR to start monitoring.
In this phishing playbook, we have used following two actions:
- block_url
- push _domain_to_refset
Phishing Attack Example
Let’s take a look at this specific example where an employee has received a phishing email from Norton Security, alerting them about the expiry of Norton Security subscription. This email includes a legitimate looking “Renew Subscription” button which leads to a malicious URL.

Upon suspicion, the email is forwarded by the employee to a dedicated inbox created for SIRP to read and ingest as a new alert
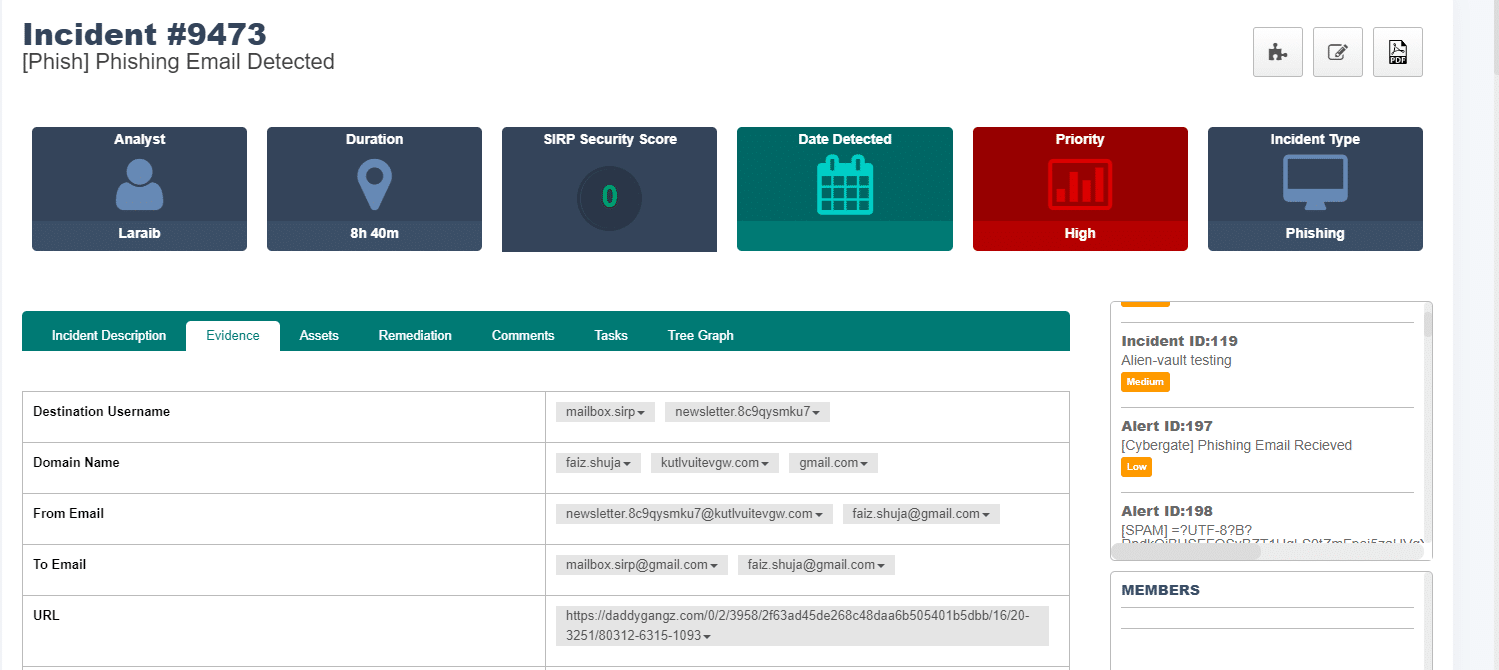
The alert is ingested and all the artifacts are automatically parsed and displayed in the Evidence tab.
Upon querying, the enrichment tools like VirusTotal and WHOisXML returns the results, confirming that the artifacts found in the email are malicious.

Since the URL found in the email is reported as a phishing URLtwice, the playbook will proceed with the remediation actions.
Playbook would first run the block_url action to block the malicious IP on the Palo Alto Firewall.

Secondly, the playbook would call push_to_refset action to push the malicious domain to IBM QRadar so that if the same domain is found in future, it will generate an alert for the analyst.

Benefits
There are multiple benefits of automating a phishing attack response:
- Free up analysts time by automating repetitive and tedious investigative actions.
- Dramatically reduce response time by automating the response actions.
- Reduce possibility of human error in a large-scale attack.
- Handle more alerts in less amount of time. Respond to phishing attacks at scale.

