
SIRP and ThreatQuotient – Extended Detection and Response with Contextualized Intelligence
September 28, 2021
Unmatched Visibility and Automation through CrowdStrike Falcon and SIRP
January 17, 2022
SIRP and ThreatQuotient – Extended Detection and Response with Contextualized Intelligence
September 28, 2021
Unmatched Visibility and Automation through CrowdStrike Falcon and SIRP
January 17, 2022Behind the Rise of the Million Dollar Zero-Day Market

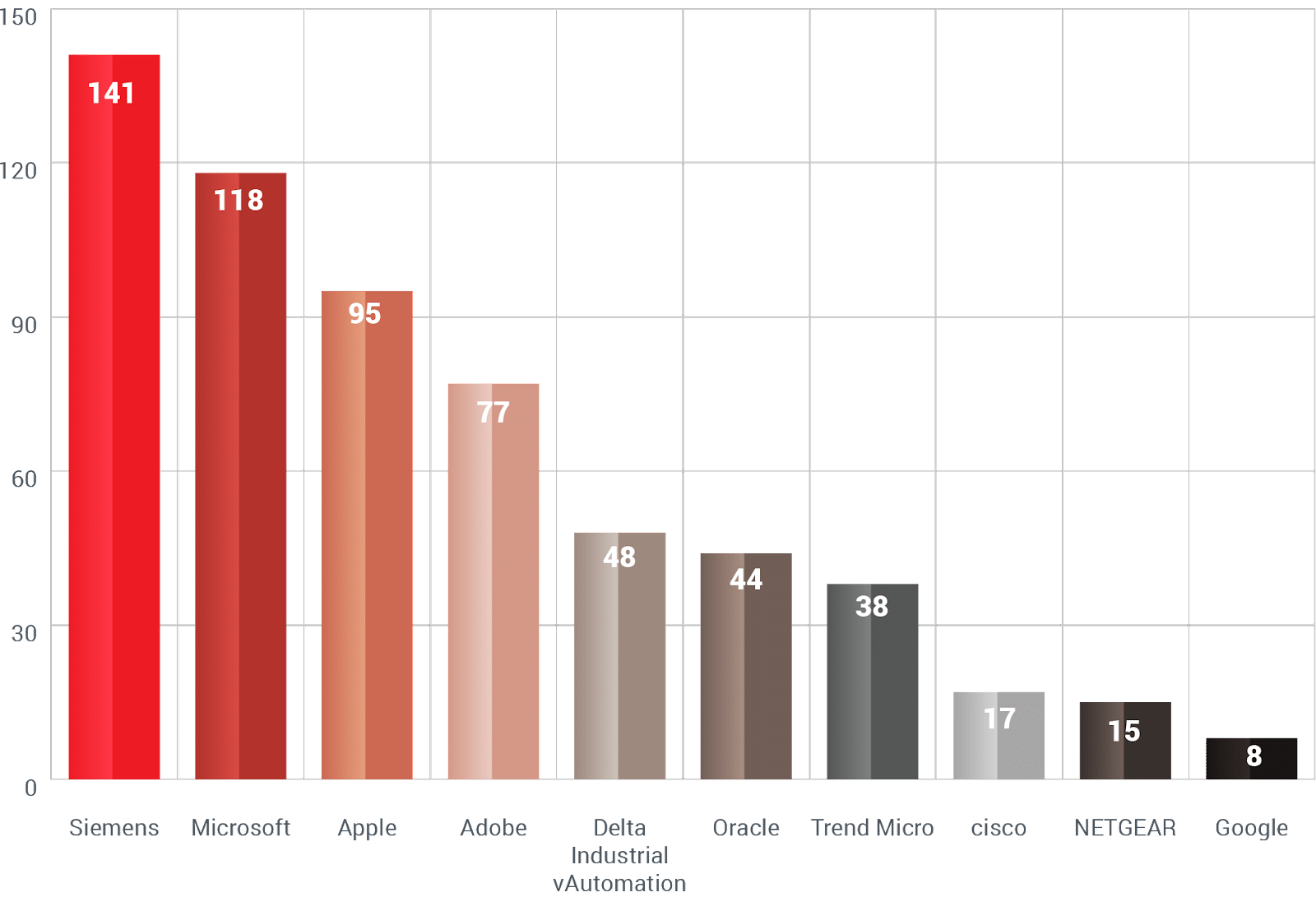
Rewterz reported in its Annual Threat Intelligence report that 2021 has proven to be the most cumulative year for Zero-Day vulnerabilities. Surpassing the numbers of 2020 and 2019. What can be attributed to this increase in reporting? Simply put, the race is, who gets to exploit the vulnerabilities, and the runners are vendors and threat actors. Most exploited Zero-Days are from vendors like Siemens, Microsoft, Apple, and Adobe.
Interestingly, these vendors hire bug bounty hunters to discover Zero-Day vulnerabilities for $2500 to $2,500,000, while these zero-days are sold to cybercriminals and novice groups for around $10,000,000. APT (Advance Persistent Threat) groups are financially or ideologically motivated, highly organized threat actors orchestrated to harm the governments and institutes of rival countries or adversaries. State-sponsored APTs may have the funds to purchase these zero-days, but even emerging criminals and groups can buy these zero-days at these expensive rates.
“The United Arab Emirates, the United States, and European and Asian powers have all poured money into the exploit industry,” says Patrick O'Neill from MIT.
A new trend in the market is also Exploit-as-a-service; cybercriminals are competing for these exploits being sold on the dark web away from prying eyes. And why shouldn’t the Zero-Days be sold online, since they have resulted in multi-million dollar losses alone in 2021?
Most Zero-Days Observed
The Two Sides of the Picture
There are two reasons for this increase in Zero-Day discovery.
-
Either technological advancements have enabled professionals in discovering and patching Zero-Days more than ever before.
-
Or, the increase in Zero-Day discoveries simply means that threat actors have gotten more active.
Either way, the disclosure of Zero-Day vulnerabilities in 2021 suggests that 2022 will welcome even more discoveries.
Why are Zero-Days so Effective?
Since systems and designs have gotten too complex and convoluted, any updates and developments must cater to millions of other interlinked systems, designs, standards, and compliances. If not, that is an exploit and vulnerability waiting to be discovered and dubbed as “Zero-Day.” These Zero-Days are then “exploited-in-the-wild” i.e. they are being utilized by hackers and threat actors to attack organizations for the destruction of data, running arbitrary codes, ransomware, and data theft.
Since Zero-Days are flaws or loopholes already present in the system in place, it makes the attack more reliable and sophisticated. They are undetected until the day they are released and therefore can be exploited while staying under the radar, which makes them highly effective for threat actors.
The Debate Behind PoCs
PoC (Proof of Concept), as the name suggests, is the demonstration and workflow of how vulnerabilities can be exploited. Researchers publish working PoCs of vulnerabilities for two reasons
-
To convince companies of security risks to speed up the patch development process.
-
To spite the organizations being affected (revenge or intent to cause harm).
Recently, the PoCs of Microsoft vulnerabilities CVE-2021-42321 and CVE-2021-41379, the PoC for the former was released by a security researcher after the patch was released, while the latter was released out of frustration of the researcher on low bounty money. The premature publication of PoCs provides threat actors with an open day to hunt and fetch their prey. “And even the technically unsophisticated actors benefit, by using that public PoC to test their skills against vulnerable software,” says a report by digital shadows.
Zero-Days Have a Huge Impact
Zero-Day vulnerabilities that are actively exploited may result in a loss of millions for organizations. Albeit financial loss is a worrisome consequence of an attack, a reputational loss can not only damage the image of the company, but it may also result in distrust among customers and end with significant damage to finances.
Since the target for threat actors is data, their first fish in the hook are credentials (usernames, passwords, and email IDs). If fallen into the wrong hands (by being uploaded on the dark web), this data can cause further damage in the shape of phishing attacks and identity theft.
When the words “zero-day attacks” are said, the first one that comes to mind is the Kaseya-REvil fiasco where the APT group asked for $70 million as ransomware. The attack originated from the exploitation of a zero-day vulnerability that allowed for authentication bypass.
Same ol’ same ol’
Although new Zero-Days vulnerabilities provide a landmine of ammunition to threat hunters and attackers, it's the old advisories that prove to be the most beneficial. Many organizations suffering from attacks usually are a victim of outdated patches or inadequate patch management. These old unpatched exploits and zero-days prove helpful for novice attackers as well.
What does it take to keep yourself safe?
A Risk-Based Approach is your best chance at keeping yourself safe.
A Risk-Based Vulnerability Management (RBVM) system not only controls the risk of vulnerabilities in an environment, but it also aims to detect and remove said vulnerabilities. It offers threat context for the potential risks brought on by infected devices, networks, and cloud infrastructures. The building blocks of RBVM are:
-
Visibility into all assets on the network or in the environment.
-
Scanning and monitoring for a wide array of attack vectors and methods.
-
Prioritizing assets based on threat context, including:
-
The asset’s value
-
The severity or criticality of the vulnerability
-
The presence of mitigation methods already in the environment
-
Prioritizing results on the basis of the identified context and mitigation techniques.
SIRP’s risk-based XDR platform provides all these services with our out-of-the-box integrations, enriched and contextualized threat intelligence, single-pane-of-glass view of incidents and reports, and incident response and vulnerability management capabilities.

