
SIRP Named Winner of the Coveted Global InfoSec Awards during RSA Conference 2021
May 17, 2021
SGBox and SIRP – Fusion of Next-Generation SIEM and SOAR
June 2, 2021
SIRP Named Winner of the Coveted Global InfoSec Awards during RSA Conference 2021
May 17, 2021
SGBox and SIRP – Fusion of Next-Generation SIEM and SOAR
June 2, 2021INTEGRATION
Elastic SIEM and SIRP - Unified Security Analysis, Enrichment, and Response

Security Information & Event Management (SIEM) and Security Orchestration, Automation and Response (SOAR) solutions perfectly complement each other. The integration between SOAR and SIEM opens up security orchestration, automated investigation, and incident response to endless possibilities.
Think of SOAR as connective tissue for your SOC; SOAR ingests alerts from security tools, assesses their cruciality, and identifies the related threat-centric cases and incident-specific response plans – all in one place.
Elastic Stack (commonly known as ELK) is composed of Elasticsearch, Kibana, Beats, and Logstash. It enables organizations with the ability to collect, monitor, analyze, and identify threats and anomalies in their data. Elastic SIEM leverages the abilities of Elasticsearch for improved speed and scale. The SIEM app enables host and network security event analysis by providing key network and host activity metrics, network and host event tables, and enables interaction with the Timeline Event Viewer.
Together, Elastic SIEM and SIRP provide signal integration to quickly identify and document any suspicious activity and gather evidence, which enables SOC analysts to accelerate incident response from start to finish.
Bidirectional integration between SIRP SOAR and Elastic SIEM enables SOC teams to orchestrate and automate response actions through detailed, relative, and predefined playbooks. It cuts back the detection, investigation, and response period 8x times.
Integration Features
-
Enhanced threat alerts with Elastic’s machine learning and alerting features combined with SIRP’s ability to detect and reduce false positives and help analysts prioritize and mitigate alert fatigue.
-
SIRP’s automated playbooks can be triggered through Elastic SIEM detection alerts for rapid orchestration of incident response across all of SIRP’s integrated tools.
-
Deeper investigation of security incidents and automated queries from SIRP to Elastic SIEM to fill holes in kill-chain investigations.
-
Visualize, assess, search, and correlate logs with Elastic SIEM features using dashboards, tree graphs, and infographic displays.
Challenges
A data breach or malware attack can topple a security team by requiring real-time threat detection and mitigation – which the team is not equipped to do. Correlating past and present events, while the analysts also scramble to gather contextual data and mitigate the threat, can take several hours. Switching between screens, lack of up-to-date information, and data silos further decelerate the response time. If the SOC analysts spend most of their time completing mundane tasks, how will the emerging threats be alleviated?
Solution
SIRP SOAR and Elastic SIEM provide an integrated solution for alert enrichment and real-time incident response. Interactive triage, threat detection, incident investigation, and automated response are only a few of the benefits of the SIRP SOAR and Elastic SIEM integration. Predefined Elasticsearch queries can also be conditioned to trigger automated playbooks in SIRP for consistent and fast triage and response. Together, SIRP and Elastic protect organizations against data breaches and extensive loss or damages.
Use Case 1: Alert Escalation and Aggregation
On its own, Elastic SIEM is able to ingest traditional logs and events data sourced from tools and devices like firewalls, servers, applications, and databases. The aggregated data and analysis are used to correlate logs and events into threat alerts. The problem, however, arises when hundreds of alerts are generated and investigated by SOC analysts every day.
Alternatively, SIRP can help organizations through aggregation and prioritization of alerts. Along with the internal alerts, external threat intelligence from various sources is also being ingested. Benefiting from these external integrations, SIRP automates the investigation and response workflows and subsequently reduces the mitigation time.
Use Case 2: Automated Response and Orchestration
With 100+ out-of-box integrations with various vendors and playbooks already present in SIRP, our SOAR becomes a powerful platform for automating responses in a multivendor environment. The automatic response can be powered within our SOAR by pushing the data generated, the insights, and the analytics within Elastic to SIRP. Conversely, SIRP can leverage Elastic for real-time data aggregation, threat orchestration, and response.
Below is an example of a Playbook that can be executed from SIRP.
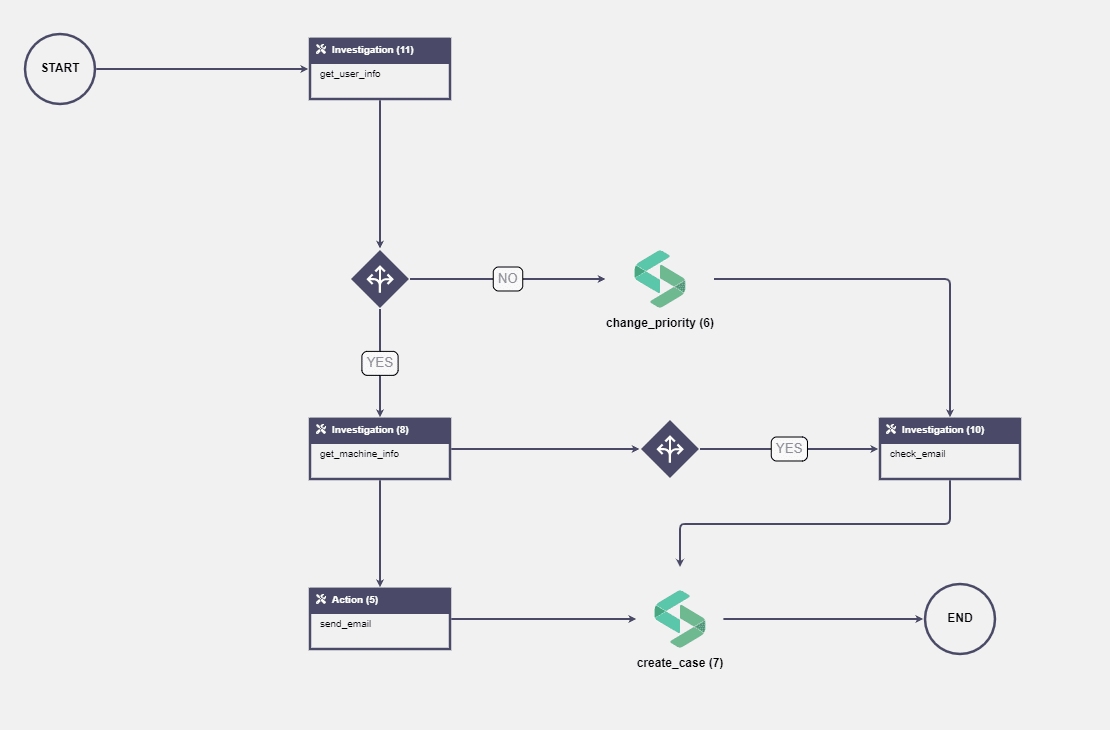
-
Once an alert is ingested in SIRP, relevant artifacts e.g. User ID and Source IP address are parsed and stored as evidence.
-
Gets user information from the Active Directory server.
-
IF the user does not belong to any critical department e.g. IT or IS.
-
Then
-
Change the alert priority to low
-
Send email notifications to the concerned department.
-
Create Case
-
Assign investigative tasks to L1 Analysts
-
ELSE the user belongs to the critical department
-
Then
-
Filter user’s machine information (CN) and email address from Microsoft Active Directory results.
-
Check IP Address/Hostname on Microsoft defender ATP for alerts.
-
Create Case with high priority
-
Send an email to the User’s manager
-
Assign investigative tasks to L2 Analysts for further investigation
Benefits
-
Manage cases in SIRP and correlate the process with Elastic SIEM to actively hunt for threats.
-
Aligned sources with Elastic SIEM to unify threats to a singular resource for case archival.
-
Investigate and quickly analyze suspicious activities with the interactive workspace offered by Elastic SIEM.
-
Pivot between data and multiple sources without screen fatigue and gather relevant data efficiently.
-
Standardize and streamline incidence response, and refine and resolve the incident lifecycle management.
-
Orchestrate and automate response actions with predefined playbooks.


