
SIRP 2020 Security Analysts Survey
August 9, 2020
FireEye and SIRP – Automated Threat Intelligence and Incident Response for Endpoint Security
August 12, 2020
SIRP 2020 Security Analysts Survey
August 9, 2020
FireEye and SIRP – Automated Threat Intelligence and Incident Response for Endpoint Security
August 12, 2020DarkOwl and SIRP - Automated Dark Web Monitoring and Investigation

The dark web is a place on the internet that’s hidden from search engines. The forums and websites on the dark web are only reachable with encrypted requests which makes it a safe haven for attackers and identity thieves. With the confidence of anonymity, identity thieves buy or sell victims personal information on these virtually invisible dark web sites, forums, and chat rooms.
Some of the data that is being exchanged on these dark web sites are names, phone numbers, email addresses, passwords, credit card numbers, fake domains, phishing pages, and more.
The Dark Web Monitoring services allows organizations to be aware of such breaches and respond (change password, expire a credit card, notify a user, etc.) as soon as they receive a notification that information has been leaked or seen on the dark web.
As with any other breach or alert, the key is to identify and respond early, before any major damage is done. This is where DarkOwl comes into play. DarkOwl is a Darknet Intelligence provider offering access to the world's largest dataset of darknet and deep web content. DarkOwl enables organizations to effectively search, monitor, and receive alerts when leaked data appears on the darknet.
Now DarkOwl customers can use SIRP’s security orchestration and automation capabilities to search, investigate and respond to data leaks occurring on the Dark Web.
Integration Features
- Run an effective incident response cycle using DarkOwl dark web search combined with SIRP risk-based SOAR capabilities.
- Search for compromised credit cards, domains, email addresses and passwords - either in real-time or as a playbook action.
- Run advanced threat hunting scenarios by searching for latest malware, CVEs, and exploits being shared on the DarkWeb.
- Automatically open cases, involve third-parties to respond to an incident based on the findings.
- Maintain excellent cyber hygiene through automated dark web monitoring and response.
Challenge
The organizational and customer information is usually the top privacy concern for the organizations. With the ever expanding footprint of digital services, protecting this information and monitoring for possible breaches poses a number of challenges. The core challenge in these situations is time to respond. For example, if you’ve found that a password of an employee has been leaked on the dark web, the real difference would be how soon you act and either change that password or lock down that email address with proper notifications.
Solution
Security teams can automate the dark web monitoring and response by creating playbooks in SIRP. These playbooks help analysts get alerts of possible leaks from Dark Owl and then define appropriate remedial actions.
Use Case 1 - Credit Card Leak Monitoring and Response
Consider an example where SIRP received an alert against a BIN number that you are monitoring on DarkOwl. Based on the predefined rules, a playbook will get executed to check if certain data has been leaked.
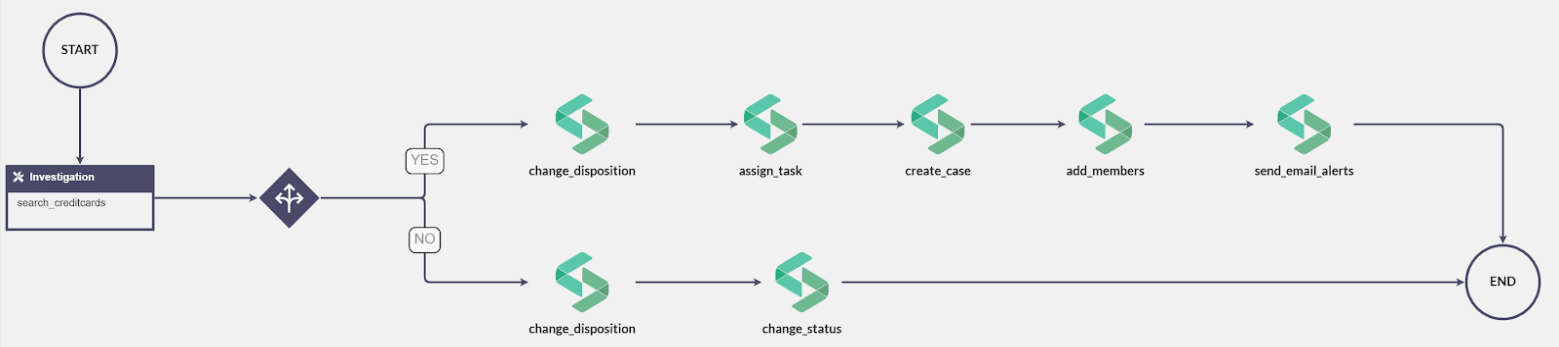
After verifying the data (BIN numbers and credit cards associated to the organization), the playbook is set to:
- Change the disposition of alert to “incident”
- Open a case
- Assign an L2 analyst along with a certain set of tasks
- Add members to the case
- Issue email notifications
The entire execution and decision flow of the playbook looks something like this:
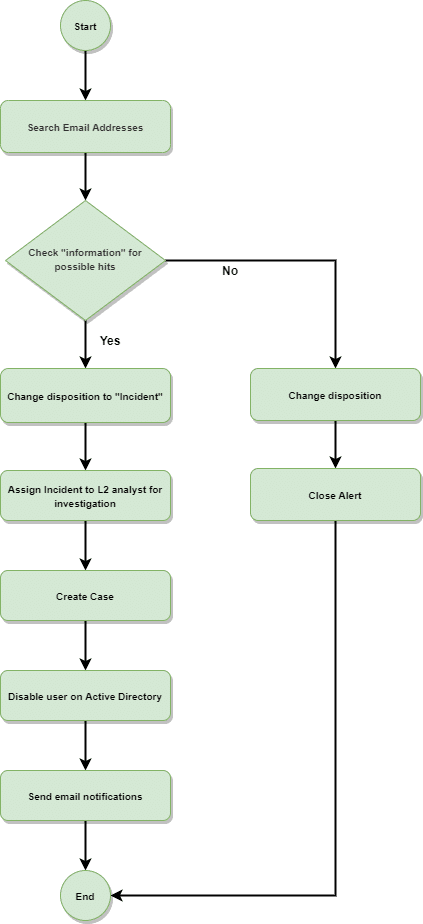
Use Case 2 - Email Address and Password Leak Monitoring and Response
Consider an example where SIRP received an alert against an email address that you are monitoring on DarkOwl.
Based on the predefined rules, a playbook will get executed to check if certain data has been leaked. After verifying the data (i.e. if received data contains references to one of the monitored email addresses), the playbook is set to:
- Change the disposition of alert to “incident”
- Open a case
- Assign an L2 analyst along with a certain set of tasks
- Disable user on Active Directory (or Force password change)
- Issue email notifications
The entire execution and decision flow of the playbook looks something like this:
Use Case 3 - Domain Investigation on Dark Web
New domains and subdomains are created as part of the normal operation of the Internet Domain Name Service (DNS). Unfortunately, bad actors commonly use newly created domains for criminal activities like spam, malware distribution, or botnet command and control (C&C). Attackers use the new domains within the first few minutes of creating them—making it difficult to build effective domain-based blocking policies.
Analysts can use SIRP playbook that uses domain reputation from DarkOwl to identify the risk score of a domain. It then uses a cloud-based security policy enforcement tool to block access to the domain.
Primary functions of the playbook are:
- Obtain domain reputation from DarkOwl to perform investigation within SIRP as an automated task.
- Search for domain details in DarkOwl using regular expressions within SIRP to access related domains, classifiers, DNS history, co-occurrences, and more.
- Get malicious domains and DNS information for an IP address from DarkOwl within SIRP, either as an automated task or in real-time.
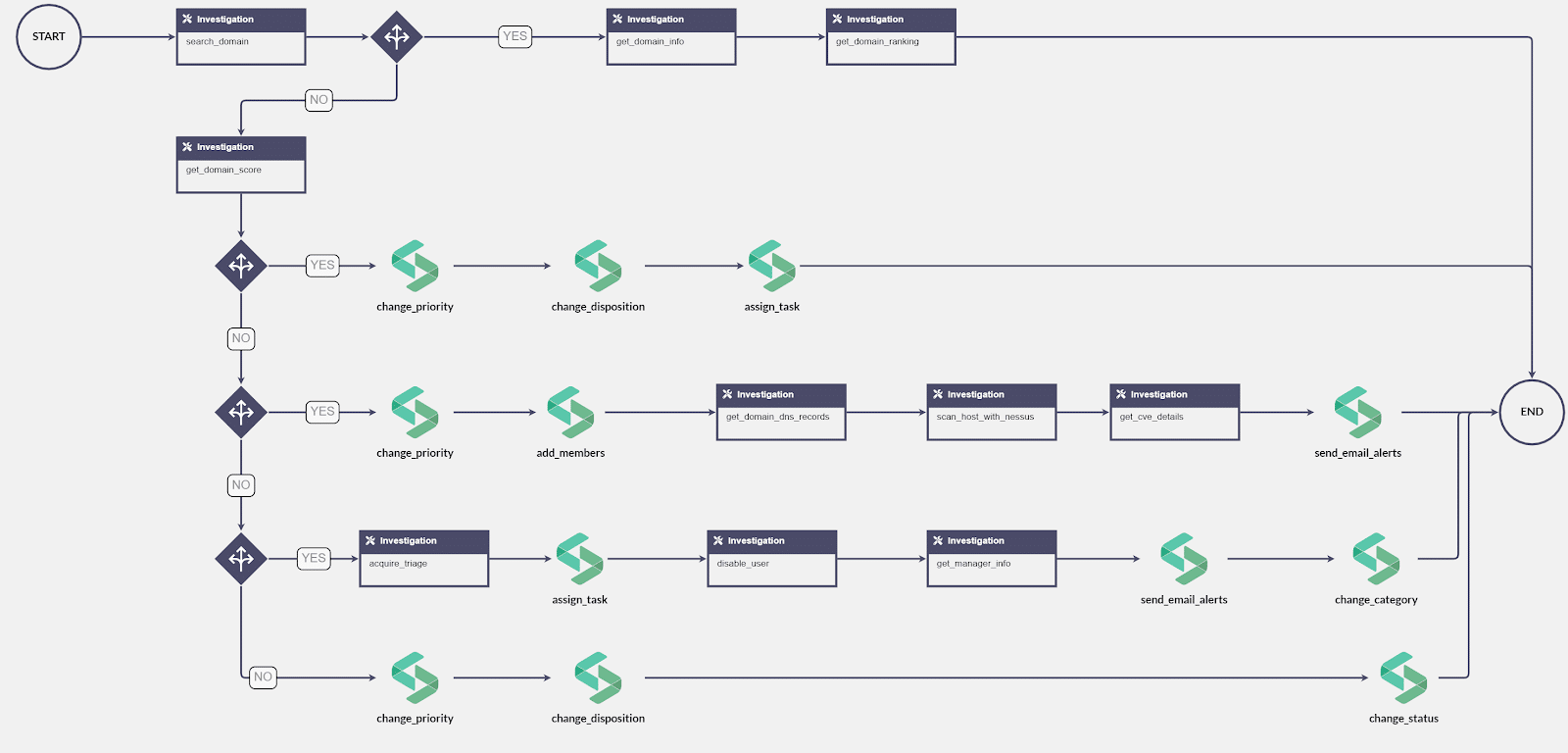
After verifying the data (i.e. Checking the “domain score”), the playbook is set to:
If domain score is equal to 3 (i.e. <30%):
- Change priority to “Medium”
- Change alert disposition to “Threat Intel” and Sub disposition to “Investigation”
- Assign tasks to analyst (e.g. Domain score rate is found as 30% which means there are some email address records have been breached and available over the dark web)
If domain score is greater than 3 but less than 6 (i.e. >30% and <60%):
- Change priority to “High”
- Create a Case
- Add members to the case
- Get domain’s DNS records from MXToolbox
- Initiate vulnerability scan on the web server
- Send Email notifications
If domain score is greater than 6 (i.e. >60%):
- Acquire triage of the web server
- Assign investigate tasks to the Analyst
- Disable user on Microsoft Active Directory
- Get user’s manager information from Microsoft Active Directory
- Send email notifications
- Change alert category to “Policy Violation” and sub category to “Information Disclosure”
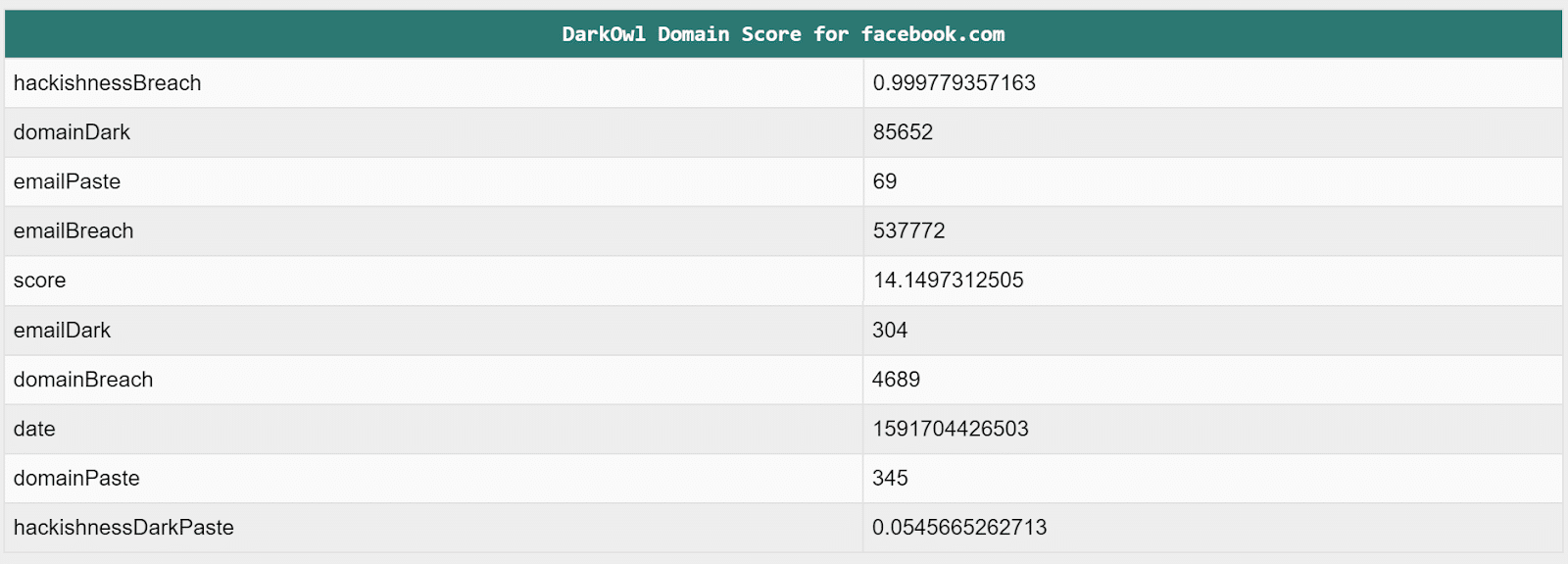
Note: DarkOwl calculates the score based on multiple factors. Greater score means greater “hackishness” of the domain.
Use Case 4 - Investigating and Responding to Document Exfiltration on Dark Web
Consider an example where SIRP received an alert against a domain name that you are monitoring on DarkOwl or an analyst searched for a domain name manually using SIRP’s automation playground. Based on the predefined rules, a playbook will get executed to take appropriate response actions.
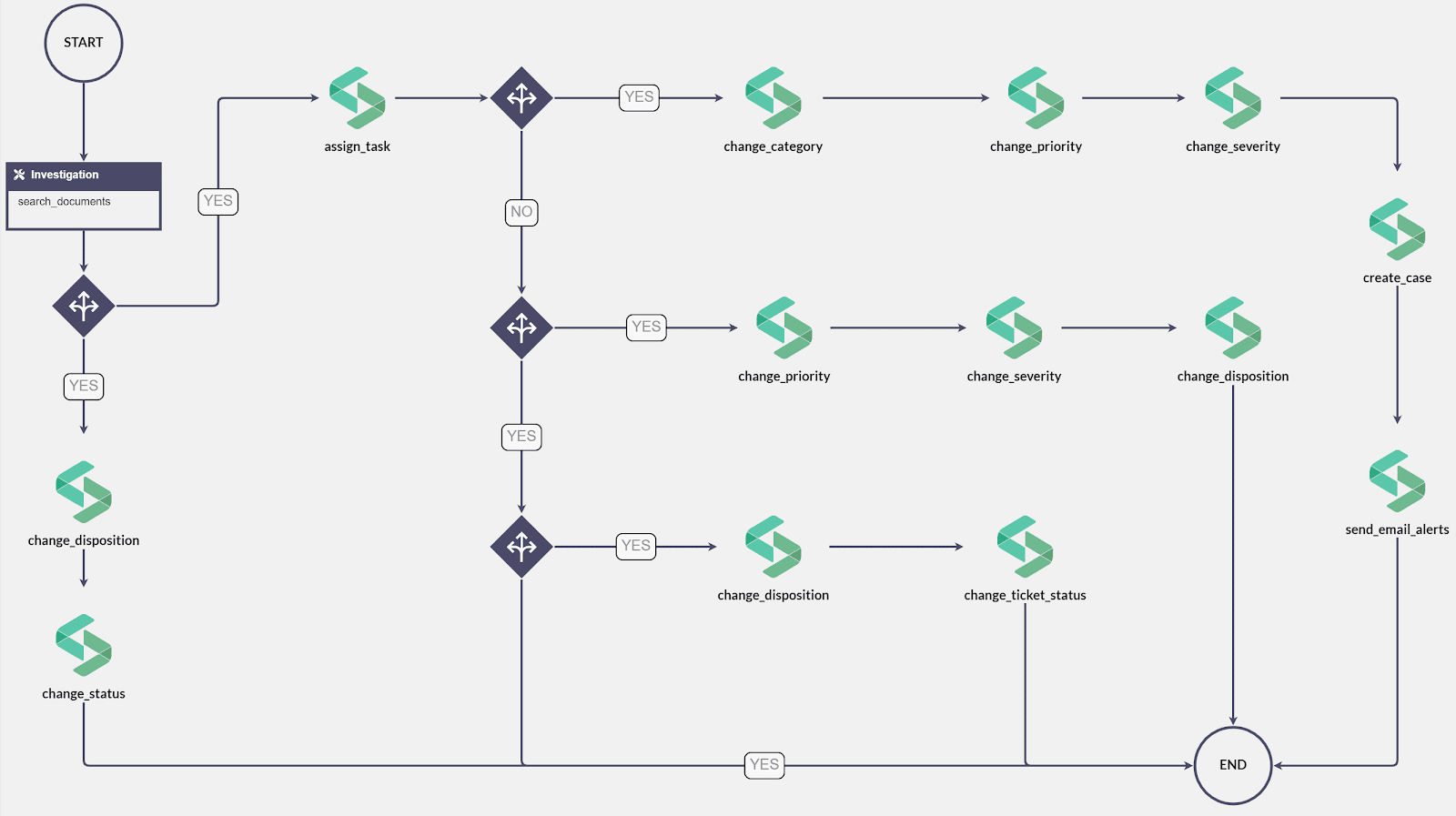
After verifying the data (i.e. Checking the “Information Tag”), the playbook is set to:
If Information Tag contains “Confidential” or “Restricted”:
- Change Category to “Policy Violation” and Subcategory to “Information Disclosure”
- Change Priority to “High”
- Change Severity to “High”
- Create a Case
- Send email notifications (e.g. Notify custodian about the document leak)
If Information Tag contains “Internal”:
- Change Priority to “Medium”
- Change Severity to “High”
- Change Disposition to “Incident” and Sub Disposition to “True Positive”
If Information Tag contains “Pubic”:
- Change Disposition to “Alert”
- Change Status to “Closed”
Benefits
With this type of integration, the time from an alert from the dark web to its response reduces dramatically. Analysts can actively monitor dark web for possible leaks leveraging DarkOwl’s monitor and search actions, and enrich their findings using 100s of other integrations available in SIRP. Other than orchestrating and automating dark web monitoring and response, analysts can also correlate the data ingested from other security technologies as well as organizational risks, asset importance, threat intelligence, and vulnerabilities.


