
Predictions for Today, 2022!
January 24, 2022
SOAR Implementation: Challenges And Countermeasures
May 17, 2022
Predictions for Today, 2022!
January 24, 2022
SOAR Implementation: Challenges And Countermeasures
May 17, 2022INTEGRATION
SIRP and Carbon Black - Unparalleled Automation and Endpoint Protection

An XDR is an improved alternative to commonly found security solutions that have their limitations. It innovates the already existing EDR and NTA with integrated threat intelligence, improved analytical capabilities of internal and external traffic, correlation and orchestration techniques, and a scalable solution that improves over time. Carbon Black (CB) and SIRP’s integration enables our XDR’s above-mentioned capabilities with its unparalleled visibility, rapid remediation on alerts, and threat detection and containment abilities.
With SIRP’s XDR and CB, the Security Operations Centers (SOCs) improve their response time due to increased speed and threat hunting qualities. The SOC analysts are less fatigued as SIRP enables partial or full automation using our automation playbooks, a single-pane-of-glass view lowers tool switching as the information appears in an easily viewable format, case management also simplifies as process details and enrichment of alerts is ingested from CB.
Challenge
A SOC analyst, without an integrated solution, runs multiple software to keep their environment secure. These solutions include an EDR, WAF, SIEM, or anti-virus. Once they receive a threat or note any malicious activity, they will first ingest behaviors related to the threat online, investigate the threat, and then take remediation steps to keep their environments safe. Now let’s multiply this threat by a thousand. This is the ballpark figure of how many threats an analyst will have to analyze to perform their job (excluding the false positives, of course).
It is imaginable how many screen switches analyzing these many threats will require. Not only will it limit the investigative abilities of the analyst but, it will also hinder their alert management and triage capabilities.
Solution
With SIRP’s XDR, the multiple steps taken to mitigate a threat are all taken using a single dashboard. Since an XDR is an accumulation of multiple platforms and software, the threat can be investigated, enriched, and mitigated directly from SIRP. Details on the processes, endpoint details, available IOCs, and history of the incident are all available to SIRP through CB. And then automated playbooks escalate the issue so that the analysts' redundant tasks get reduced.
Integration Features
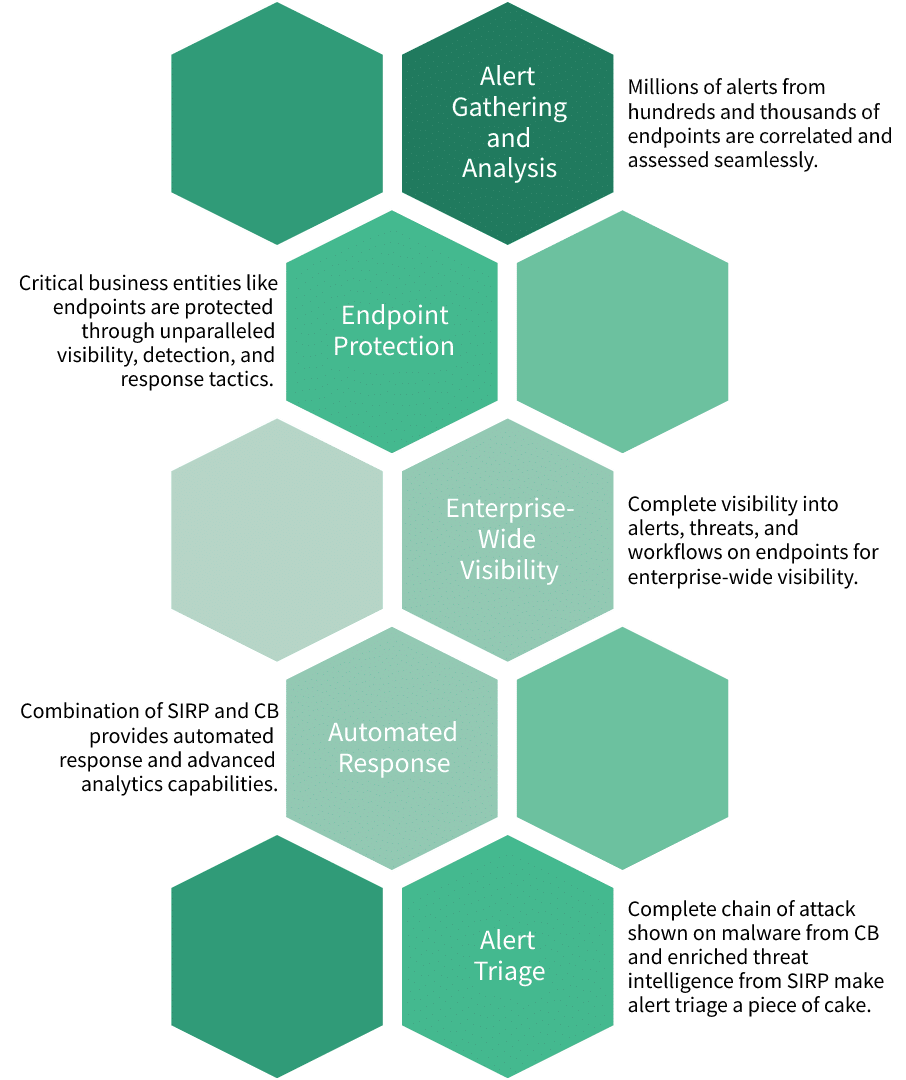
Use Cases
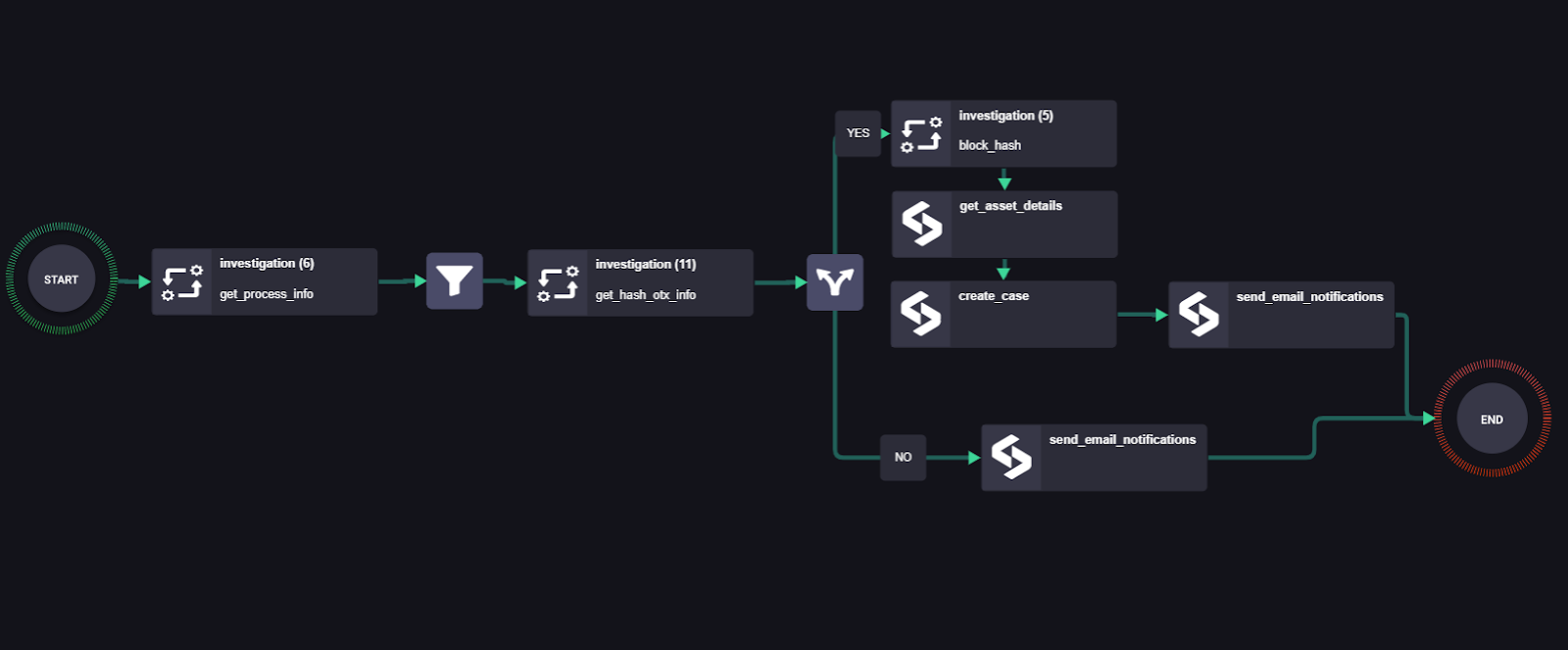
Case 1: Hash Banning
In this scenario, an alert containing malicious hash is inserted through the threat intelligence feeds using automated playbooks. In this playbook, the parsed hash is analyzed, enriched, and then blocked if found malicious - all using SIRP and CB. The playbook is set to perform the following actions.
- Process information is obtained through our Carbon Black actions.
- The filter is applied to
- The hash reputation is investigated using open threat exchange like Virustotal.
IF the hash is found to be malicious:
- The hash is blocked through Carbon Black actions.
- Asset details are fetched.
- A case is created and relevant members are added.
- Email notifications to relevant parties are sent.
Else
- Change Sub disposition to “False positive”
- Change status to “Close”
- Send email notifications to relevant parties.
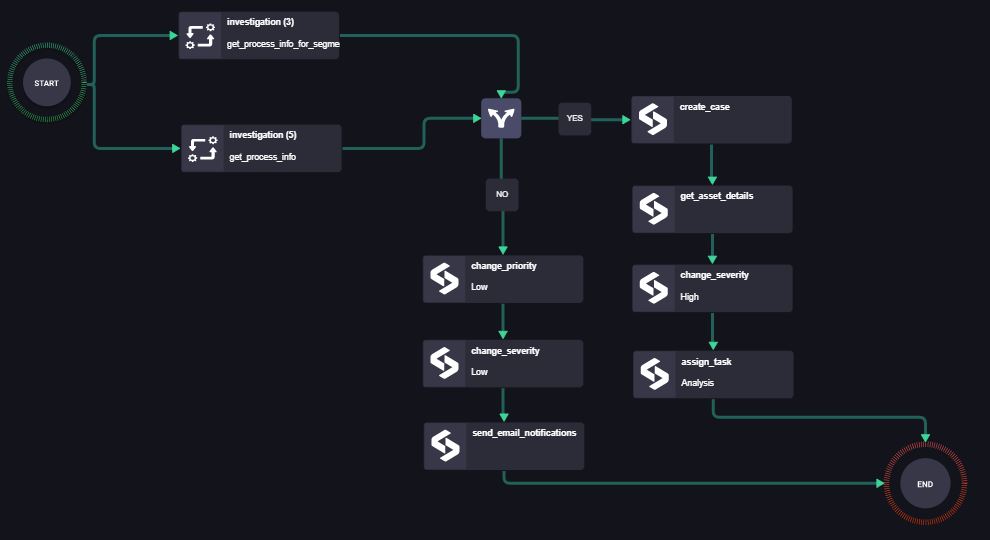
Case 2: Automate Investigation for Behavioral Anomalies Using CB
SIRP can leverage Carbon Black for automated investigation of behavior anomalies. In this scenario, an asset performs a task or repetition of tasks which are unusual for it (For instance drive-by downloads). Behavior-based alerts are generated at Carbon Black and ingested into SIRP through “get_alerts” action. Below is the Playbook that will be executed from SIRP.
- Process information for the asset and for Process Information in segments is collected from Carbon Black actions.
IF the process information indicates that the actions are malicious:
- A case is created in SIRP.
- Asset details are fetched from SIRP.
- Change severity to “High”.
- Task is assigned to the Analyst for further analysis.
Else
- Change priority to “low”.
- Change severity to “low”.
- Email notifications are sent to relevant parties.
Benefits
- Faster and improved threat detection and mitigation capabilities.
- Rapid response to active threats made possible.
- Unfiltered enterprise-wide visibility on endpoints, with corrective and mitigation actions.
- Prioritization of alerts according to the severity of the detected threat.
- This integration is an all-in-one solution for all threat detection and remediation with SIRP and CB, that improves SOC performance.

