
Managing Web Application Firewall (WAF) response with SIRP SOAR
June 24, 2021
What SOAR Brings To SOC KPIs
July 30, 2021
Managing Web Application Firewall (WAF) response with SIRP SOAR
June 24, 2021
What SOAR Brings To SOC KPIs
July 30, 2021SOAR Use Case - Responding to PrintNightmare

The end of June brought upon a new nightmare (pun intended) for Microsoft when multiple proofs of concepts (PoC) of the Microsoft Windows Print Spooler vulnerability (CVE-2021-1675) were released on Github. Microsoft tried to remediate the issue by releasing patches for the CVE on Patch Tuesdays. But alas, the PoC was. deemed critical and assigned a separate CVE, CVE-2021-34527. This working PoC was named PrintNightmare by the security researcher that posted it online, and that is where the name comes from.
This vulnerability impacts all supported and extended security update versions of Microsoft Windows. The vulnerability can be exploited through Remote Code Execution (RCE) by attackers that take advantage of the fact that the service is enabled by default on most Windows systems. Python and C++ PoC have been released for RCE and C# rendition has been, released for LPE (Local Privilege Escalation). And successful exploitation of this vulnerability allows the attacker to run arbitrary commands on the infected system with SYSTEM privileges. This can be used to install new programs on the system; view, change, delete data and create new users with full rights.
The function, RpcAddPrinterDriverEx(), is used to install the printer drivers on the system as the Microsoft Windows Print Spooler service is unable to restrict access to this function.
Mitigation Techniques
Microsoft has released security updates and workarounds for the vulnerability in their CVE-2021-34527 advisory. Implementation of the workarounds may prevent inbound remote printing operations. Following are steps for the mitigation (if a patch is installed),
Determine if the Print Spooler service is running
Run the following:
Get-Service -Name Spooler
After it is determined that the service is currently running or not disabled, apply one of the below-mentioned options to either disable the service or disable inbound remote printing through Group Policy.
Option 1 - Disable the Print Spooler service
If disabling the Print Spooler service is appropriate for your organization, use the following PowerShell commands:
Stop-Service -Name Spooler -Force
Set-Service -Name Spooler -StartupType Disabled
Impact of workaround Disabling the Print Spooler service disables the ability to print both locally and remotely.
Option 2 - Disable inbound remote printing through Group Policy
You can also configure the settings via Group Policy as follows:
Computer Configuration / Administrative Templates / Printers
Disable the “Allow Print Spooler to accept client connections:” policy to block remote attacks.
The service must be restarted for the changes to take effect.
Proof of Concept (POC)
Using “rpcdump.py” potential vulnerable hosts can be discovered, as shown in the figure below, the scanned endpoint is running Print System Remote Protocol.

This PowerShell script performs Local Privilege Escalation (LPE) with the PrintNightmare attack technique. The next action from the adversary will add a new user to the local administrator’s group.
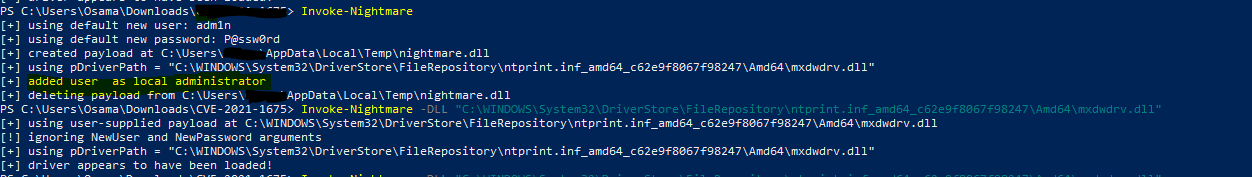
Detection using Windows Events:
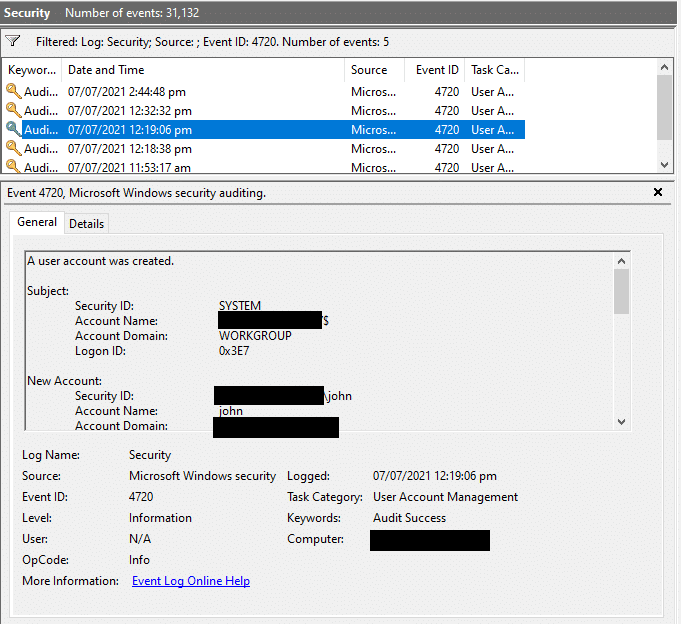
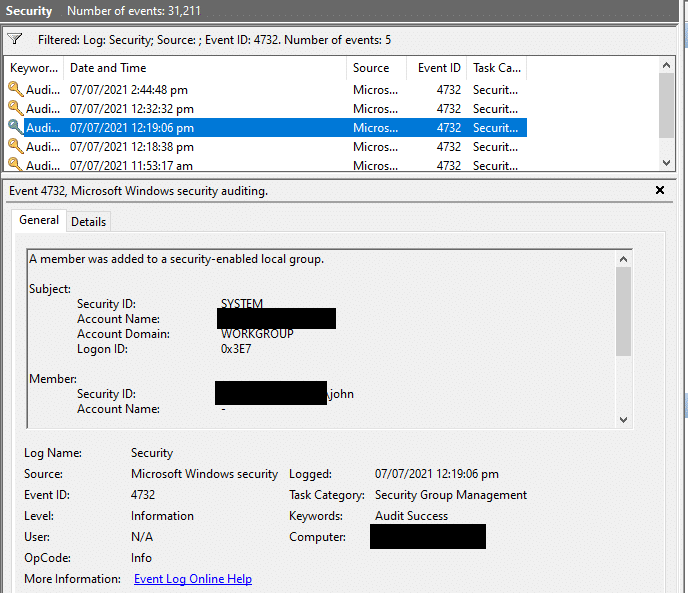
To detect this activity, security teams should monitor Windows event ID 4720 for local user creation followed by created user addition in local admin group in event ID 4732.
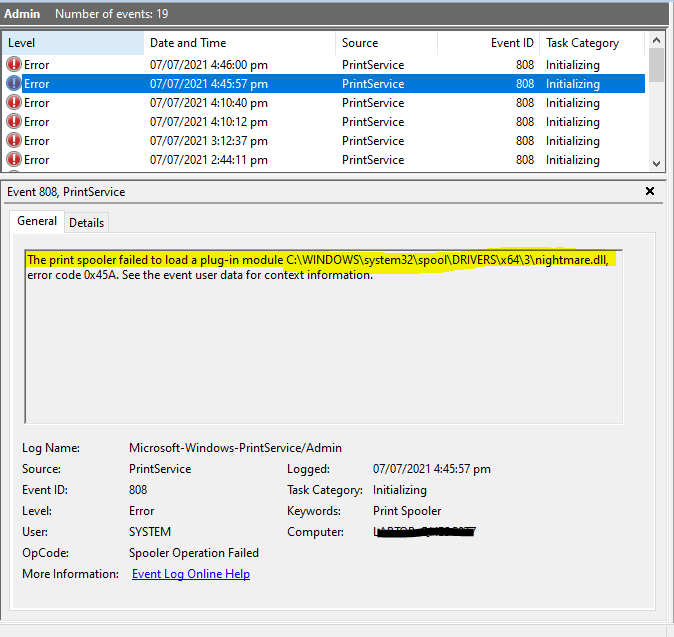
By enabling logging of Microsoft Print Service (Microsoft-Windows-PrintService/Admin), Event ID 808 is logged when the print spooler fails to load a plug-in module.
By enabling logging of Microsoft Print Service operational events (Microsoft-Windows-PrintService/Operational), Event ID 316 is logged when printer drivers are added or updated.
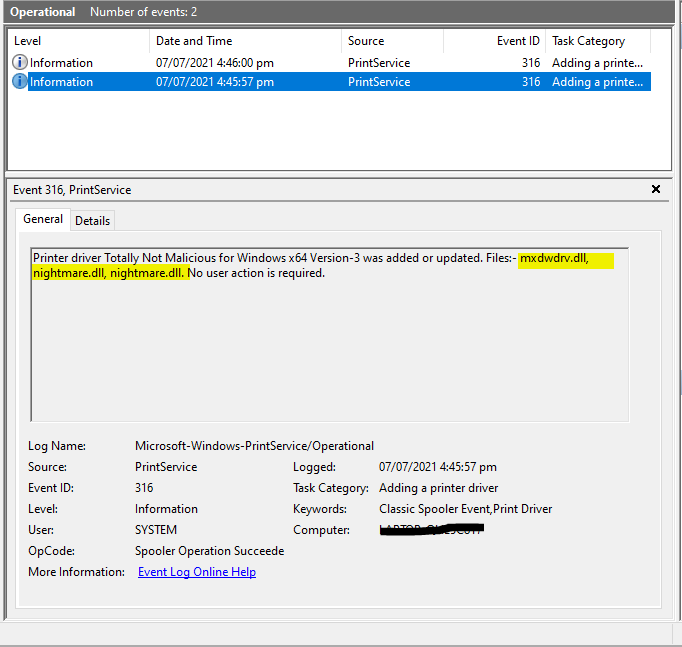
Detection Logic for Use Cases/SIEM rules
Following pseudo logic can help detection this activity:
- The process contains 'spoolsv.exe' and
- Image path contains 'C:\Windows\System32\spool\drivers\x64\'
- Filename does not contain any of these
- 'UNIDRV.DLL'
- 'wdlres.dll'
- 'hpygidres20.dll'
- 'hpygidUI20.dll'
- 'ADUIGP.DLL'
- 'FXSTIFF.DLL'
- 'FXSAPI.DLL'
- 'x5lrs.dll'
- 'MXDWDRV.DLL'
- 'FXSUI.DLL'
- 'FXSRES.DLL'
- 'PrintConfig.dll'
- 'FXSDRV.DLL'
To investigate any exploit attempts, the following script will be helpful to collect relevant information from event viewers:
“Get-WinEvent -LogName 'Microsoft-Windows-PrintService/Admin' | Select-String -InputObject {$_.message} -Pattern 'The print spooler failed to load a plug-in module'”
Using Automation for Quicker Detection and Response
SIRP can accelerate the discovery of known vulnerabilities by leveraging the power of automation. SIRP’s multiple integrations with Vulnerability Scanners, SIEMs, and EDRs enable us to do that. The vulnerability scanning tool scans the filename assets for the identification of a vulnerability.SIEM is then used to correlate the events. EDR accelerates the detection and response processes.
-
- The first step is to check if the functions to be exploited are available on the potentially affected system.
- If the service is accessible, run the following commands to either disable or block the service.
-
Stop-Service Spooler
REG ADD "HKLM\SYSTEM\CurrentControlSet\Services\Spooler" /v "Start" /t REG_DWORD /d "4" /f
OR
Uninstall Print-Services
Uninstall-WindowsFeature Print-Services
-
-
- Detection of the file can be done by selecting the following (default) filenames used in the PoC:
-
TargetFilename|contains:
· 'C:\Windows\System32\spool\drivers\x64\3\old\1\123'
· 'C:\Windows\System32\spool\drivers\x64\3\New\'
-
- Detection of the file can be done by selecting the following (default) filenames used in the PoC:
SIRP PrintNightmare Playbook covers the following tasks:
-
-
- Checking if the Print Spooler service is enabled and vulnerability exists in the system.
- Mitigation actions:
- Manual disablement of Print spooler services.
- Restriction of ACLs.
- Installation of patches and updates.
- Initiating Scans – detection of vulnerable systems.
- Enrichment of data – through logs, threat intelligence, and searching for affected systems.
- Escalation to L2 Analyst – Task is assigned to the L2 analyst for further investigation and decision making.
-

The playbook is carried out in the following way:
The playbook is triggered on SIRP
IF the Print Spooler Service is enabled:
-
-
- Notify IT Team to take Manual Action - Disable Print Spooler Service
- Notify IT Team to take Manual Action - Install Microsoft patch for spooler service
- Notify IT Team to take Manual Action - Restrict ACL
-
Then
-
- Initiate a scan on the affected endpoint using a vulnerability scanner.
- Get events related to event IDs 808 and 31017 using Qradar SIEM
- Enrich CVE Details from Vulndb and CVE Search
- Assign Task to L2 Analyst to Investigate with relevant security tools and enriched data in the ticket.
Automated Incident Response Actions
SIRP integrates with several tools allowing you to automate multiple remedial actions. For example,
Integrating SIEM to automate alerts ingestion
- IBM QRadar
- RSA NetWitness
- Splunk
- Elastic SIEM
Integrating Threat Intelligence for enrichment
- CrowdStrike
- DarkOwl
- BLueliv
Integrating EDR and EPP solutions for remedial actions
- Windows Remote Management
- block file path
- copy file
- get file
- delete file
- FireEye HX
- Block Hash
- Isolate System
- Acquire File
- Acquire Triage
- Trend Micro Apex Central
- Isolate system
- Create Scan
- Block/Unblock IP
- Windows LDAP
- Enable / Disable User
Conclusion
Aforementioned are some of the integrations that enable SIRP’s SOAR platform to detect and remediate vulnerabilities and exploits in the wild like PrintNightmare. SIRP’s rapid detection and response capabilities empower incident response and SOC teams to save hours of manual labor by taking care of the detection and enrichment process itself.
To see how the SIRP SOAR platform can help your organization decrease response times, tackle cyber risk, and improve visibility, get in touch today to arrange your personalized demonstration.
References
Beaumont, K., 2021. Zero-day for every supported Windows OS version in the wild — PrintNightmare. [online] DoublePulsar. Available at:
Msrc.microsoft.com. 2021. Windows Print Spooler Remote Code Execution Vulnerability. [online] Available at:
Roth, F., 2021. PowerShell one-liner to highlight CVE-2021-1675 exploitation attempts.
Stewart, C., 2021. CVE-2021-1675 - PrintNightmare LPE (PowerShell). [online] GitHub. Available at:

